Cybercrime is hands-down one of the quickest growing crimes around the globe and it continues to impact organizations from all industries. Being protected from cyber-attacks is becoming more and more challenging. While cyber criminals are constantly looking for ways to take advantage of your security vulnerabilities, it’s very difficult for most organizations to keep up with them.
Cybercrime is hands-down one of the quickest growing crimes around the globe and it continues to impact organizations from all industries. Being protected from cyber-attacks is becoming more and more challenging. While cyber criminals are constantly looking for ways to take advantage of your security vulnerabilities, it’s very difficult for most organizations to keep up with them.
This fourth article in the serieswritten by Joe Coleman, cybersecurity officer at Bluestreak Consulting™, will give you a better understanding of some general cybersecurity best practices for all businesses, and a few tips for what you should and shouldn’t do.
This column is found in Heat Treat Today's December 2022 Medical and Energy print edition.

Cybersecurity Officer
Bluestreak Consulting™
Source: Bluestreak Consulting™
What Are the Risks of Having Poor Cybersecurity?
It’s difficult to remain 100% protected 100% of the time, but the risks from failing to have proper cybersecurity are hefty. The risks include: malware that can delete your entire system; the selling of your data or your customers’ data; an attacker hacking your system and altering files; an attacker using your computer to attack others; or an attacker stealing your credit card information and making unauthorized purchases.
12 Best Practices To Reduce the Chance of Cyberattacks
Follow these cybersecurity best practices to minimize the risks of cyberattacks and improve your cybersecurity:
- Use complex passwords: Use at least 12 to 16 characters, including letters (upper and lower case), numbers, and special characters. Remember to change your passwords frequently.
- Keep software up to date, including antivirus and antimalware: Install software patches as soon as they become available. Also, be sure to enable automatic virus definition updates to ensure maximum protection against the latest threats.
- Utilize a firewall: Firewalls may be able to prevent some types of attacks by blocking malicious code before it can infect your computer. Enable and properly configure the firewall as specified.
- Enable Multi-Factor Authentication (MFA) or 2-Factor Authentication (2FA): This gives you an additional layer of protection that helps to verify that you are an authorized user.
- Be suspicious of unexpected emails: Phishing emails are currently one of the biggest risks to a user. The goal of a phishing email is to gain information about you, steal money from you, or install malware on your device (if you click on something in the email).
-

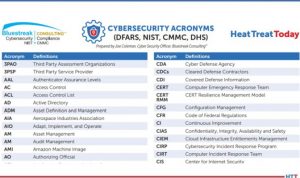
Click the Image TO Download More Than 350 Cybersecurity Acronyms Use VPNs to ensure connections are private: To have a more secure and private network connection, use a VPN (virtual private network). Your connection will be encrypted, and your private information protected.
- Look for HTTPS on websites (instead of just HTTP): On websites that do not use HTTPS, there’s no guarantee that the information between you and the site’s servers is secure.
- Scan external storage devices: External storage devices have the same risk as internal storage devices. Always scan external storage devices for malware before accessing them.
- Train your employees: If your cybersecurity program has any chance of working, make sure your employees are well trained and always using security best practices. It only takes one mistake. Educate your staff to be aware and on the lookout for different types of malicious social engineering (including a simple phone call asking for a username and/or password).
- Backup your important data: Critical data can be lost with security attacks. Make sure you backup your important data frequently to the cloud or local storage device (preferably multiple devices).
- Don’t use public networks: Avoid public networks or use a VPN to connect. All of your information is vulnerable on public networks at hotels, coffee shops, airports, and other similar locations.
- Use secure file-sharing to encrypt data: When sharing sensitive or confidential information, always use a secure file-sharing solution. If emails are intercepted, unauthorized users will have access to your data.
Improve Your Cybersecurity Weaknesses
NIST SP 800-171 is an excellent best practice, even if you are not in the DoD downstream or military-related supply chain, to ensure your data and your customer’s data is always secure.
My fifth article in this Cybersecurity Desk series will be: “Performing Your Basic & Your Final NIST 800-171 Assessments.”
About the Author:
Joe Coleman is the cybersecurity officer at Bluestreak Consulting™, which is a division of Bluestreak | Bright AM™. Joe has over 35 years of diverse manufacturing and engineering experience. His background includes extensive training in cybersecurity, a career as a machinist, machining manager, and an early additive manufacturing (AM) pioneer. Joe will be speaking at the Furnaces North America (FNA 2022) convention, presenting on DFARS, NIST 800-171, and CMMC 2.0. Contact Joe at joe.coleman@go-throughput.com.
 Find heat treating products and services when you search on Heat Treat Buyers Guide.com
Find heat treating products and services when you search on Heat Treat Buyers Guide.com